KMS
Feature
AWS Key Management Service(KMS)
- a managed service that makes it easy for you to create and control the encrypton keys used to encrypt your data.
- The master keys that you create in AWS KMS are protected by validated cryptographic modules.
- AWS KMS is integrated with most other AWS services that encrypt your data with encryption keys that you manage.
Scenario
- You are working as a Solutions Architect for a government project in which they are building an online portal to allow people to pay their taxes and claim their tax refunds online. Due to the confidentiality of data, the security policy requires that the application hosted in EC2 encryps the data first before writing it to the disk for storage.
In this scenario, which service would you use to meet this requirement?- A) AWS KMS API
- the scenario mentions that you have to encrypt data before writing it to disk for storage. What this means that you will have to temporarily store the data in memory and not persist it on the disk, then encrypt it immediately before finally storing it. You can configure your application to use the KMS API to encrypt all data before saving it to disk.
- Security Token Service(STS) : enables you to request temporary, limited-previlege credentials for IAM users or for federated users.
- EBS encryption : the application could not use this service to encrypt data that it writes on the disk.
- You are leading a software development team which uses serverless computing with AWS Lambda to build and run applications without having to set up or manage servers. You have a Lambda function that connects to a MongoDB Atlas, which is a popular Database as a Service (DBaaS) platform and also uses a third party API to fetch certain data for your application. You instructed one of your junior developers to create the environment variables for the MongoDB database hostname, username, and password as well as the API credentials that will be used by the Lambda function for DEV, SIT, UAT and PROD environments.
Considering that the Lambda function is storing sensitive database and API credentials, how can you secure these information to prevent other developers in your team, or anyone, from seeing these credentials in plain text? Select the best option that provides the maximum security.- A) Create a new KMS key and use it to enable encryption helpers that leverage on AWS Key Management Service to store and encrypt the sesitive information
- If you wish to use encryption helpers and use KMS to encrypt environment variables after your Lambda function is created, you must create your own AWS KMS key and choose it instead of the default key.
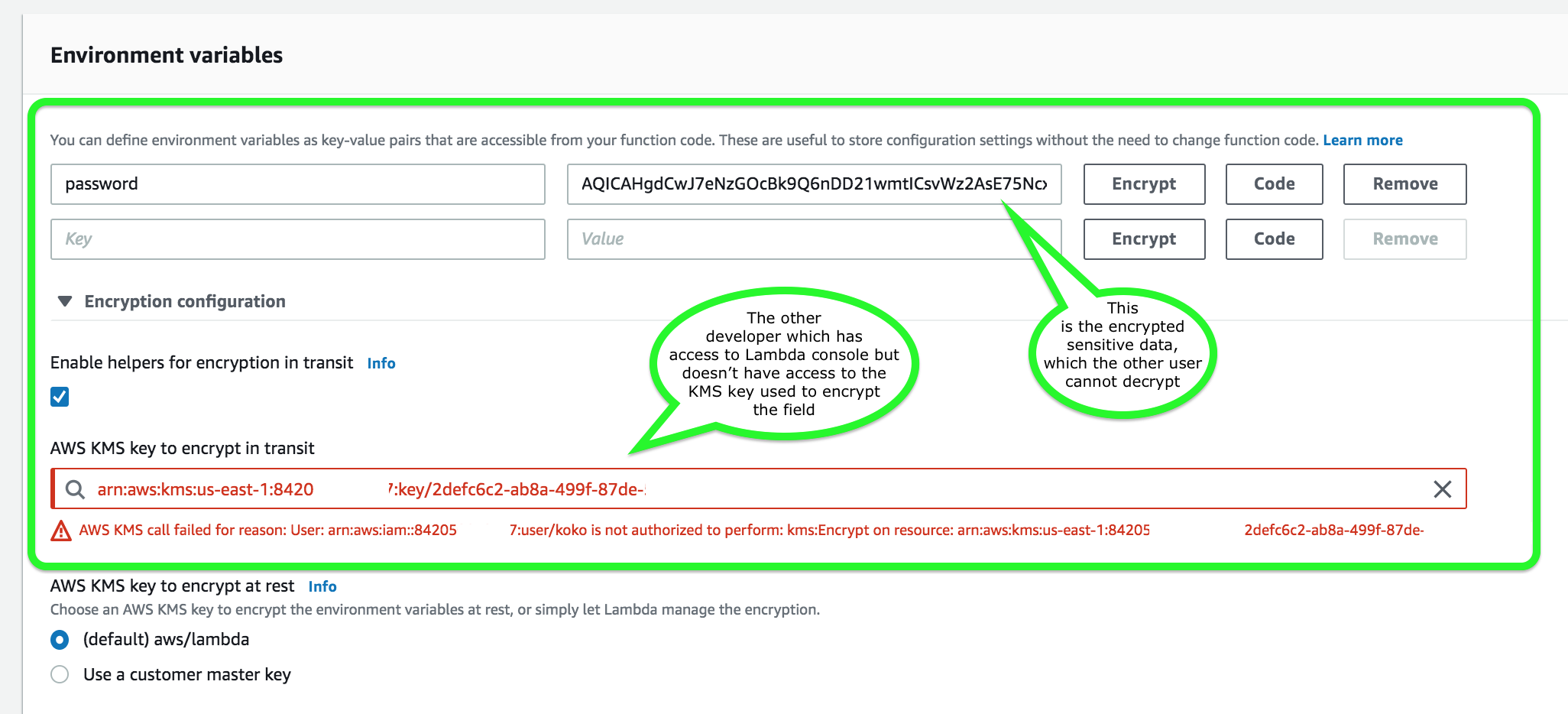
- although Lambda encrypts the environment variables in your function by default, the sensitive information would still be visible to other users who have access to the Lambda console. This is because Lambda uses a default KMS key to encrypt the variables, which is usually accessible by other users. The best option in this scenario is to use encryption helpers to secure your environment variables.
- SSL encryption on CloudHSM : enabling SSL would encrypt data ONLY when in-transit.
- A media company has an Amazon ECS Cluster, which uses the Fargate launch type, to host its news website. The database credentials should be supplied using environment variables, to comply with strict security compliance. As the Solutions Architect, you have to ensure that the credentials are secure and that they cannot be viewed in plaintext on the cluster itself.
Which of the following is the most suitable solution in this scenario that you can implement with minimal effort?- A) Use the AWS Systems Manager Parameter Store to keep the database credentials and then encrypt them using AWS KMS. Create an IAM Role for your Amazon ECS task execution role and reference it with your task definition, which allows access to both KMS and the Parameter Store. Within your container definition, specify secrets with the name of the environment variable to set in the container and the full ARN of the System Manager Parameter Store parameter containing sensitive data to present to the container.
- although you can use Docker Secrets to secure the sensitive database credentials, this feature is only applicable in Docker Swarm. In AWS, the recommended way to secure sensitive data is either through the use of Secrets Manager or Systems Manager Parameter Store.
- it is not recommended to store sensitive credentials in S3.